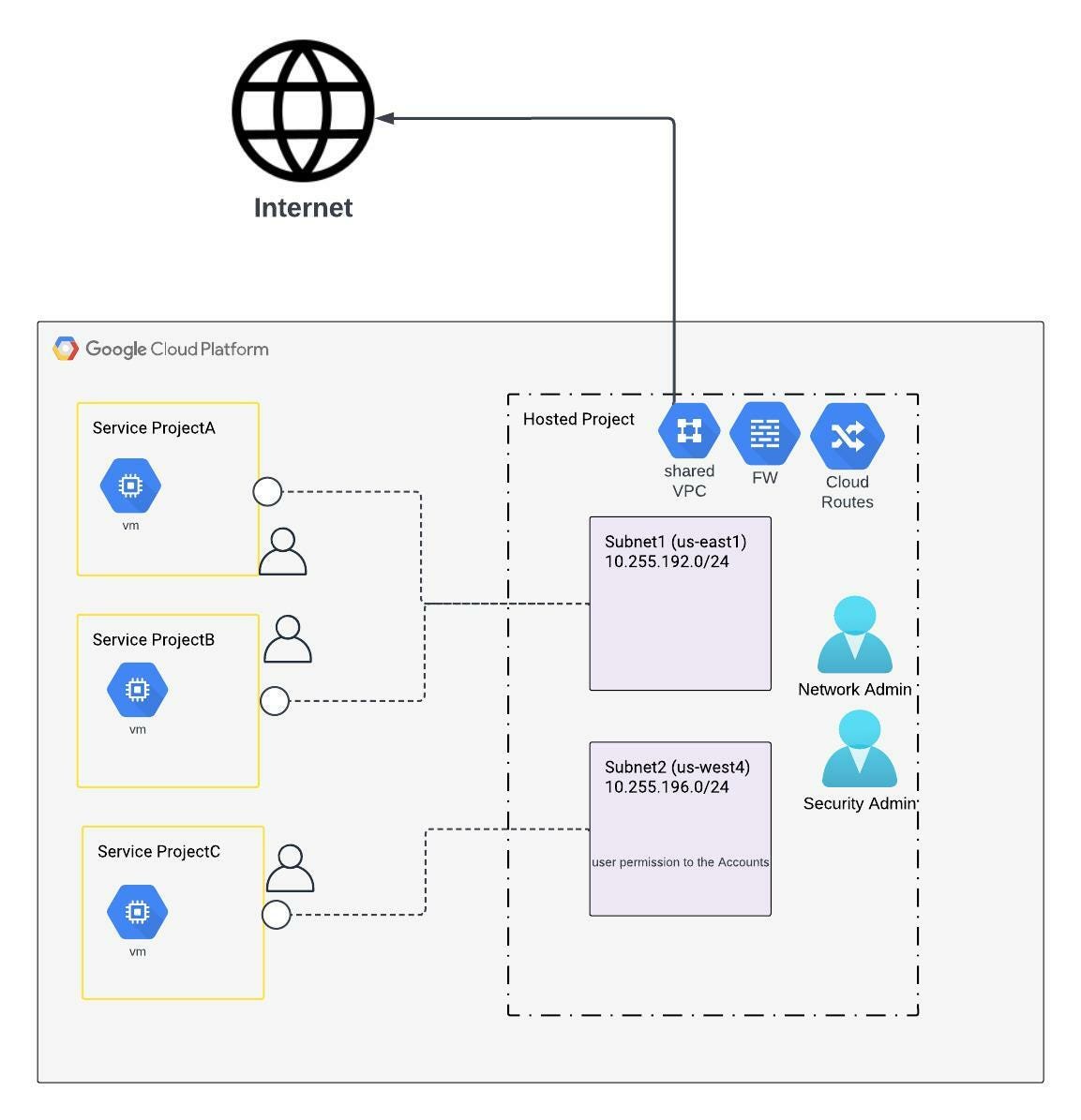
Connecting Internet of Things (IoT) devices in a secure, virtual network, crucial for remote operation. A key infrastructure for modern IoT deployments.
A virtual private cloud (VPC) network, geographically separated from the core network, enables secure communication and management of IoT devices. This isolation is particularly valuable for devices operating outside of a traditional data center or corporate network. Think of a fleet of sensors monitoring a remote oil pipeline, or smart meters deployed across a vast geographical area. These sensors need a way to securely report data back to a central hub. A dedicated VPC facilitates this secure communication channel. It establishes a virtual boundary, preventing unauthorized access and ensuring data integrity. This structure allows the infrastructure to scale and adapt to evolving needs for remote device management. The key advantage is that the private network remains isolated from the public internet, enhancing security.
Such a structure offers several significant benefits. Increased security, critical for sensitive data transmitted by the IoT devices, is paramount. By isolating the IoT devices within their own dedicated network, the risk of malicious attacks and data breaches is reduced. Furthermore, geographical separation enhances operational resilience. A problem in one region or with a specific network connection won't directly affect other remote devices. The scalability of this network model allows for the addition of new devices and management complexity without requiring major restructuring of the entire infrastructure. It's a flexible framework critical for the future of industrial and commercial IoT deployment.
This configuration, encompassing the benefits of security, scalability, and resilience, presents a cornerstone for the expansion of remote IoT systems. Moving forward, we will explore the various technical considerations in designing such VPC networks for specific IoT applications.
Remote IoT VPC Network
Secure, scalable connectivity is paramount for remote Internet of Things (IoT) deployments. A Virtual Private Cloud (VPC) network is a crucial enabling technology in this context. Understanding its key components is vital for effective implementation.
- Security
- Scalability
- Isolation
- Remote Access
- Data Integrity
- Management
- Resilience
These key aspects underpin a robust remote IoT VPC network. Security measures, like encryption and access controls, are essential for sensitive data transmission. Scalability allows the network to accommodate a growing number of devices. Isolation from public networks prevents unauthorized access. Remote access enables management and monitoring from distant locations. Data integrity ensures the accuracy of information collected by the IoT devices. Efficient device management simplifies updates and maintenance. Resilience ensures continued operation in the face of network disruptions. For instance, a remote pipeline monitoring system necessitates a scalable, secure, and geographically dispersed VPC network to safeguard data transmission and operations across varied locations.
1. Security
Security is paramount in remote IoT VPC networks. The inherent sensitivity of data collected by IoT devices, coupled with their often geographically dispersed deployments, necessitates robust security measures. Protecting these networks from unauthorized access and malicious attacks is critical for maintaining operational integrity and preventing data breaches.
- Network Segmentation and Isolation
A well-designed VPC network employs network segmentation, isolating IoT devices from broader corporate networks or the public internet. This confinement reduces the attack surface, minimizing the impact of a potential compromise on one device or sensor. An example might involve an oil pipeline monitoring system where sensor data is confined to its own VPC, preventing a breach on one sensor from impacting others or the wider corporate network.
- Data Encryption and Confidentiality
Encrypting data transmitted within the VPC network ensures confidentiality and protects sensitive information from eavesdropping or interception. This is crucial for IoT devices handling confidential data like financial transactions or sensitive operational information. Real-world application examples involve smart grids transmitting data about energy usage or industrial control systems managing production processes.
- Access Control and Authentication
Implementing strict access controls and robust authentication mechanisms limits access to the VPC network. Only authorized personnel or systems can interact with the IoT devices and data, mitigating the risk of unauthorized access or tampering. Examples include user authentication and authorization protocols or role-based access control systems.
- Regular Security Audits and Penetration Testing
Regular security assessments, including penetration testing and vulnerability scans, are vital to identify and address weaknesses in the VPC network. Proactive detection and remediation of security vulnerabilities minimize the potential for compromise. This aspect is especially critical for adapting to evolving security threats.
These security considerations are integral to the proper functioning of a remote IoT VPC network. Robust security measures, implemented proactively, minimize the risk of unauthorized access and data breaches, ensuring the reliability and integrity of operations in these geographically dispersed deployments.
2. Scalability
A remote IoT VPC network's scalability is crucial for accommodating the increasing volume of devices and data generated in distributed deployments. Adapting to future expansion needs while maintaining performance and security is paramount. This adaptability directly impacts the overall effectiveness and longevity of IoT infrastructure.
- Dynamic Resource Allocation
The ability to dynamically provision and allocate network resources, such as bandwidth and virtual machines, is essential for handling fluctuations in device activity. A smart grid system, for example, experiences varying energy consumption patterns throughout the day and across seasons. A scalable network can adjust resources to meet these fluctuations without performance degradation or significant downtime, ensuring uninterrupted data transmission and control.
- Horizontal Scaling and Replication
Expanding the network by adding more resources, such as servers or storage, without requiring a complete overhaul of the existing infrastructure, is a key aspect of scalability. This horizontal scaling allows the network to handle increases in data volume and device density. A fleet management system for autonomous vehicles, where new vehicles are constantly being added, benefits from a scalable system enabling the seamless integration of additional devices and data streams without performance bottlenecks.
- Auto-scaling and Monitoring
Automated scaling mechanisms adjust network resources in response to real-time demand. Sensors deployed across a vast agricultural landscape for weather monitoring need a dynamic network response to maintain connectivity and data flow during periods of increased data traffic, such as during a storm. Monitoring of key network metrics allows for proactive adjustments, ensuring efficient and effective resource utilization.
- Modular Design and Extensibility
A modular network design allows for the addition of new components and functionalities without significant disruptions to existing systems. Industrial applications, such as remote asset monitoring in oil and gas fields, might require the addition of new sensors or functionalities in the future, necessitating a network design that accommodates this flexibility. A scalable system allows for the integration of new technology and functions while retaining existing network stability.
In summary, scalability in a remote IoT VPC network is fundamental to its long-term success. The ability to handle increasing data volumes, device counts, and changing demands ensures continued reliability and effectiveness. A well-architected, scalable system will be better equipped to meet the challenges and opportunities presented by the continued growth of the IoT in diverse environments.
3. Isolation
Isolation is a critical component of a remote IoT VPC network, acting as a protective barrier against security threats and ensuring data integrity. The inherent distributed nature of IoT deployments, characterized by geographically dispersed devices, necessitates a robust isolation mechanism. This isolation safeguards sensitive data transmitted by devices operating in potentially hostile environments, such as remote industrial sites or public spaces. For example, a system monitoring pipeline integrity requires a secure, isolated VPC network to prevent unauthorized access to critical operational data.
The isolation offered by a VPC network creates a secure virtual boundary. This boundary acts as a fortress, containing the IoT devices and their data within a controlled environment. Within this secure space, sensitive data transmitted by sensors, actuators, and other devices remains protected. This isolation prevents unauthorized access, ensuring confidentiality and preventing data breaches. Consider a network of smart meters in a city's grid: Isolation within a dedicated VPC network safeguards their data from wider network vulnerabilities, protecting the system's integrity and the city's critical infrastructure from unauthorized intrusion.
Without effective isolation, remote IoT deployments become vulnerable to various threats. Data breaches can compromise sensitive information and disrupt operations. Malicious actors could potentially gain unauthorized access to critical systems, impacting safety and leading to financial losses. For example, a compromised smart home system could lead to physical intrusions or financial fraud. Isolation, therefore, is not just a desirable feature but a fundamental requirement for the reliability and security of any remote IoT network. Understanding the crucial role of isolation in a remote IoT VPC network is paramount for implementing secure and resilient IoT deployments in diverse and potentially hazardous environments. Properly implemented isolation helps safeguard data and operations, enabling secure, reliable, and efficient IoT deployment.
4. Remote Access
Remote access is indispensable for managing and monitoring remote IoT devices within a Virtual Private Cloud (VPC) network. Effective remote access facilitates crucial tasks such as device configuration, data retrieval, and system updates. The ability to interact with and control these devices from a central location is essential for optimal operational efficiency in geographically dispersed systems. For instance, in a pipeline monitoring system, remote access enables technicians to remotely diagnose equipment malfunctions, adjust sensor settings, and retrieve critical data without physically visiting the remote site.
The secure nature of a VPC network is intrinsically linked to the effectiveness of remote access. A VPC isolates the IoT devices from the public internet, enhancing security and minimizing the risk of unauthorized access. This secure isolation, combined with strong authentication and authorization protocols, is paramount when considering sensitive data. Without a robust remote access capability facilitated by the VPC structure, managing and maintaining complex IoT deployments across vast geographical areas becomes highly challenging and potentially risky. Real-world examples include agricultural sensor networks collecting weather data, where remote access enables farmers to monitor crop health and adjust irrigation schedules remotely. Likewise, in industrial settings, remote access allows maintenance personnel to diagnose and address equipment issues in real-time without physical presence, thereby minimizing downtime and maximizing operational efficiency.
In summary, remote access is a critical component of a remote IoT VPC network, enabling efficient management and monitoring of distributed IoT devices. The secure isolation offered by a VPC facilitates secure remote access capabilities. Understanding this critical relationship between remote access and the VPC network is essential for effectively deploying, managing, and maintaining complex, geographically distributed IoT infrastructure. This includes addressing potential security risks and establishing efficient data access protocols to maintain operational integrity and resilience in a variety of applications.
5. Data Integrity
Data integrity is crucial for the reliability and trustworthiness of information generated and transmitted by Internet of Things (IoT) devices within a remote Virtual Private Cloud (VPC) network. Maintaining data accuracy, completeness, and consistency is essential to ensure proper operation and decision-making, particularly in applications requiring precise data interpretation. Errors or manipulations in data directly impact system performance and decision-making processes.
- Data Encryption and Confidentiality
Robust encryption protocols within the VPC network protect data from unauthorized access and modification during transmission. This ensures confidentiality, safeguarding sensitive information from interception or tampering. Examples include encryption of sensor readings from a remote oil rig or medical data from wearable devices. Maintaining data integrity in these scenarios is vital for operational safety and patient privacy. Compromised data can lead to significant safety risks, incorrect diagnoses, and potentially financial losses.
- Data Validation and Integrity Checks
Implementing validation procedures and integrity checks at various stages of the data lifecycle ensures the accuracy and completeness of data. Checks can include data type verification, range verification, and consistency checks across multiple data streams. For instance, sensors monitoring water quality must validate data ranges, ensuring that readings remain within acceptable parameters. Errors detected via checks trigger alerts or corrective actions to maintain system integrity.
- Data Backup and Recovery Mechanisms
Redundant data storage and robust backup procedures in the VPC ensure data survivability during network outages or hardware failures. In remote locations, data loss due to a power outage or natural disaster can have severe repercussions. For industrial or critical infrastructure monitoring, restoring operational capability requires reliable data backup and recovery. Failure to maintain data backups jeopardizes system continuity and potential operational issues. A properly functioning recovery mechanism mitigates significant risks.
- Data Version Control and Audit Trails
Implementing version control and maintaining comprehensive audit trails helps in tracking data modifications and identifying anomalies. Understanding historical data changes enables effective troubleshooting and analysis in case of discrepancies. This is crucial for systems monitoring environmental variables or tracking equipment performance. Clear historical records ensure accurate analysis and enable effective decision-making, critical for timely intervention and adjustments.
Ensuring data integrity within a remote IoT VPC network is critical for various applications. Accurate, reliable, and secure data is essential for informed decision-making and smooth operation. The mechanisms listed above contribute significantly to maintaining the integrity of data, minimizing errors, and safeguarding the trustworthiness of data throughout its lifecycle within the remote IoT VPC. Without adequate attention to data integrity, reliability and trustworthiness of remote IoT deployments significantly decrease, leading to potential operational problems and security vulnerabilities.
6. Management
Effective management of remote IoT devices within a Virtual Private Cloud (VPC) network is crucial for operational efficiency and security. The geographical dispersion of these devices necessitates sophisticated management tools and strategies to ensure smooth functioning, data integrity, and timely maintenance. Appropriate management practices are fundamental for the effective operation and longevity of any remote IoT deployment.
- Device Provisioning and Configuration
Efficiently provisioning and configuring new devices within the VPC environment is essential. This involves automated onboarding procedures, secure device authentication, and standardized configurations. Remote management tools streamline these processes, reducing setup time and minimizing manual intervention. For example, deploying sensors across a vast agricultural field requires a standardized method to configure each sensor and integrate it into the central VPC network. This automated process ensures seamless data collection and reduced human error.
- Remote Monitoring and Diagnostics
Continuous monitoring of device health and performance is critical. Remote access and monitoring tools provide insights into device status, identifying potential anomalies or malfunctions early on. Real-time alerts facilitate proactive intervention and maintenance, minimizing downtime. Applications such as industrial automation, where equipment failure can lead to severe safety risks or production losses, emphasize the importance of immediate detection of any issues. A remote monitoring system within a VPC enables swift responses and minimizes disruptions.
- Data Collection and Analysis
Managing the vast amount of data generated by numerous IoT devices requires specialized tools for efficient data collection and comprehensive analysis. Appropriate storage, retrieval, and analysis mechanisms are critical. A secure, centralized data repository within the VPC allows for effective data analysis. Examples include predictive maintenance in manufacturing, where insights into equipment performance aid in anticipating potential failures and scheduling maintenance proactively. The insights derived from this data analysis support informed decision-making, optimize resource utilization, and prevent costly equipment downtime. A robust data management system within the VPC enables comprehensive analysis.
- Security Updates and Patching
Regular security updates and patching of IoT devices are crucial for maintaining system integrity. Automated mechanisms for delivering updates to distributed devices are essential in a remote VPC network. This minimizes vulnerabilities and mitigates the risk of cyberattacks. Examples include securing smart grids against cyberattacks. Proactive updates and patching prevent unauthorized access and ensure the security of remote infrastructure and the integrity of data collection. A robust and secure management platform allows for seamless application of security patches, bolstering security posture.
Effective management is fundamental to the successful operation of a remote IoT VPC network. Robust management practices enhance operational efficiency, minimize downtime, and maintain security. A well-designed management system, integrated with the VPC infrastructure, enables real-time monitoring, efficient data analysis, and the implementation of appropriate security measures. Ultimately, sound management practices translate to higher system reliability and resilience, enabling the full potential of remote IoT applications.
7. Resilience
A remote Internet of Things (IoT) Virtual Private Cloud (VPC) network's resilience is paramount. Its ability to withstand disruptions, maintain functionality during failures, and recover swiftly from adverse events directly impacts the reliability and trustworthiness of the entire system. Geographic dispersion, inherent in many IoT deployments, amplifies the need for a resilient network design. This resilience ensures continuity of operations even when components or connections fail.
- Redundancy and Failover Mechanisms
Redundancy, achieved through multiple network paths and redundant servers, is crucial. A single point of failure can cripple the entire system. Failover mechanisms automatically switch to backup resources when primary components fail, preserving functionality. Consider a pipeline monitoring system; if one connection is lost, the system must seamlessly switch to another, ensuring constant monitoring and preventing critical data loss.
- Geographic Dispersion and Network Diversity
A geographically distributed network, by its nature, minimizes single points of failure. Interruptions in one region do not necessarily bring down the entire network. This diversity is critical for maintaining functionality even if parts of the infrastructure are affected by natural disasters or network outages. For instance, a geographically dispersed network monitoring agricultural sensors will continue functionality even if one region experiences a natural disaster, ensuring continuity of critical data.
- Data Backup and Recovery Procedures
Robust data backup and recovery mechanisms are essential. Data loss can have severe repercussions, leading to operational disruptions, financial losses, or safety hazards. The system must be able to restore functionality swiftly and recover lost data in case of system failures. This is crucial in systems where data integrity is paramount, like medical IoT networks or industrial automation systems.
- Adaptability and Scalability to External Events
The network must adapt to changes in infrastructure and external events. Sudden spikes in data traffic, network congestion, or environmental changes might require dynamic adjustments to maintain functionality. A system monitoring a remote power grid needs to accommodate fluctuations in energy consumption. Adaptability to such changes ensures operational resilience to unforeseen events.
In conclusion, a remote IoT VPC network's resilience depends on a combination of robust redundancy, geographic diversification, reliable backup procedures, and adaptability. The ability to withstand disruptions, maintain connectivity, and recover quickly is not just desirable but critical for the successful and reliable operation of many modern IoT applications in critical infrastructure and industrial settings. This resilience directly contributes to the network's overall trustworthiness and operational efficiency.
Frequently Asked Questions
This section addresses common questions and concerns regarding remote IoT Virtual Private Cloud (VPC) networks. These networks are crucial for secure and reliable operation of Internet of Things (IoT) devices across diverse geographical locations. Understanding the fundamental aspects of these networks is essential for effective deployment and management.
Question 1: What is a remote IoT VPC network, and why is it needed?
A remote IoT VPC network is a virtual private cloud dedicated to securely connecting and managing IoT devices in geographically dispersed locations. It isolates these devices from the public internet, enhancing security. This isolation is vital for handling sensitive data and maintaining operational integrity. The need arises from the increasing deployment of IoT devices in remote areas, such as industrial facilities, agricultural fields, or utility grids, where traditional network architectures may not be sufficient or secure.
Question 2: How does a remote IoT VPC network enhance security?
A remote IoT VPC network isolates devices from the public internet by creating a dedicated virtual network. This reduces the attack surface and limits potential vulnerabilities. Strong authentication mechanisms, data encryption, and network segmentation further enhance security, preventing unauthorized access to sensitive data and maintaining the integrity of system operations. The use of virtual private networking (VPN) technologies and secure protocols further strengthen the protective perimeter of the network.
Question 3: What are the key benefits of using a remote IoT VPC network?
Key benefits include enhanced security, scalability, and resilience. Data breaches are mitigated through isolation, and the network can easily adapt to increases in the number of devices. Geographic distribution minimizes the impact of disruptions in one location, ensuring continued operation. Improved management tools and remote access simplify device management and maintenance tasks. Increased efficiency and reliability are consequential aspects of such a network.
Question 4: What factors influence the design of a remote IoT VPC network?
Factors such as the sensitivity of data, the geographical distribution of devices, the volume of data generated, and the specific needs of the application influence the design. Security considerations, scalability requirements, and the need for remote access significantly impact architectural decisions. Considerations for disaster recovery, network redundancy, and system availability directly affect the implementation of the remote IoT VPC network. Careful planning and design are vital for ensuring successful deployment.
Question 5: What are the potential challenges in implementing a remote IoT VPC network?
Challenges include the complexity of managing a geographically dispersed network, security considerations when connecting remote devices, high initial investment in infrastructure, and the need for specialized expertise in network design and maintenance. Addressing these challenges requires detailed planning, careful consideration of security protocols, and a robust understanding of the specific needs of the deployment. Specialized knowledge of IoT device connectivity and security protocols is crucial.
In summary, remote IoT VPC networks offer a robust solution for secure and reliable IoT deployments. Understanding the architecture, benefits, challenges, and design considerations is crucial for effective implementation and management. These considerations ensure long-term success in various applications, including remote monitoring and control in critical infrastructure environments.
Next, we will explore specific use cases and deployment strategies for remote IoT VPC networks, highlighting their practical application and implementation details.
Conclusion
The exploration of remote IoT Virtual Private Cloud (VPC) networks reveals a critical infrastructure component for secure and reliable operation of geographically dispersed Internet of Things deployments. Key aspects, including security, scalability, isolation, remote access, data integrity, management, and resilience, are crucial for success. Robust security measures, such as data encryption, network segmentation, and access control, are indispensable for safeguarding sensitive data and preventing unauthorized access. Scalability allows the network to accommodate expanding device deployments and data volumes, maintaining operational efficiency as the system grows. Isolation provides a secure virtual boundary, protecting the network from broader threats. Effective remote management tools and procedures streamline device configuration, monitoring, and maintenance, optimizing operational efficiency. The ability to quickly recover from network disruptions and adapt to external factors is crucial for maintaining uninterrupted operation. Data integrity safeguards the accuracy and reliability of information transmitted and processed by IoT devices, ensuring informed decision-making and system reliability. This architecture is integral for ensuring the trust and reliability of data, essential in numerous applications. Understanding and appropriately implementing these components is critical to deploying and maintaining robust, scalable, and secure remote IoT systems.
The future of remote IoT deployments hinges significantly on the effective implementation of robust and scalable VPC networks. Addressing current and emerging security vulnerabilities, combined with anticipatory planning for system scalability and resilience, will be paramount in enabling the widespread adoption of IoT technologies across critical infrastructure and diversified environments. Careful consideration of security, performance, management, and adaptability is essential for continued reliability and effectiveness in remote IoT applications. The implications for various sectors, from industrial automation to environmental monitoring, are substantial, emphasizing the importance of proactive design and implementation strategies.
You Might Also Like
Ingenuity Baby Swing Recall 2024: Important InformationMaria Victoria Henao: Colombian Champion | Inspiring Stories
Best Tonmya Products & Reviews
Safely & Securely Connect Your Raspberry Pi
Anna Strout: Bestselling Author & Literary Star
Article Recommendations
- The Unveiling Of Jay Cutler A Bodybuilders Family Legacy
- Xochitil Gomez Height How Tall Is She
- Jessica Ussery Net Worth 2024 A Deep Dive